The electronic devices of our home in the service of the informant!
Concerned about the security of communications and sensitive data has now reached global levels, we sometimes forget that the "spy" may be inside our home.
And to be things that would never cross our minds, like our coffee machine let's say!
Let's think about something simple: do the devices we keep in our household collect data on how we use them? Are they connected to the Internet? If so, they can easily watch us!
This is because mobile devices, our television and, more recently, other home electronics can be easily connected to a network that locates our activities. And this is not a bad thing. The thing escapes when these networks are hacked, with information about our habits and behaviors becoming accessible to people with bad intentions.
And it is exactly the same technological innovation - which loosens our hands - that makes us vulnerable to those who can take advantage of the leaps of technology!
With that in mind, let's look at appliances and other home systems that may be spying on us now that we are talking, or used for such purposes in the future…
- TV

Have you ever wondered how our TV remembers what programs we have watched, what we intend to watch, but also for how long we watched the last episode of our favorite series before we fell asleep sweetly on the couch? It is no secret that he can do all this through an internet connection. And that is exactly where her weakness lies!
Network and communications security company ReVuln proved last year that it can easily hack manufacturers' online platforms by gaining access to user data, installing viruses on TVs and any interconnected device, while at the same time making it difficult to collect all personal data stored on the TV.
They were even able to open the camera built into the TV, thus watching the viewers who were watching TV! The manufacturers responded by claiming that they were shielding their nets on a daily basis and fixing the flaws.
- Dishwasher, dryer, toaster, clock radio and remote control

No, we are not crazy, and it may sound like a science fiction scenario, but the future is bleak. In fact, when these are heard from the mouth of the former head of the CIA, David Petraeus, things acquire another dynamic. So common home appliances that are now (or very soon) connected to the Internet, such as the dishwasher, coffee maker and tumble dryer, will be able to collect data about their users.
Connecting to the Internet helps manufacturers deal with failures and problematic features while improving the efficiency of the devices. At the same time, it allows or will be able to allow the user to operate his devices via mobile phone, laptop and tablet, which is not a bad thing at all. The downside is that this data can be used by "insiders" to locate the user and know when he is at home and when he is not, while selling his consumer habits to companies (something that is already happening).
Petraeus even claimed that this technology would transform the landscape of espionage, "changing our beliefs about privacy and security of communications", buttering the bread of cybercriminals…
- Lights

It is the same technology that allows the monitoring of our home appliances that can enable would-be spies to control the lights of our homes. Fast-paced "smart" homes, where all electronic devices and systems will be remotely controlled via smartphone and PC applications, can solve our hands, but not without the obvious risk: beyond locating our daily schedule , would-be burglars will be able to completely control the lighting system of the house, which means that they will be able to easily turn off the lights before invading the house…
- Heating and air conditioning

The "smart" thermostats record the heating and cooling habits of the user, learn his preferences and adjust accordingly the desired temperature (with the minimum possible consumption) freeing the person from this tedious task. You can even adjust or change the options - via the Internet - when you are away from home. How many conveniences are now in the hands of the user! But come on, there have already been incidents with hackers who "played" with the thermostat, adapting it to their fraudulent needs. Burglars and spies can easily imagine doing the same…
- Alarms

For years, home security systems have been connected to the service provider's control center, offering the maximum possible coverage. Of course, there are many alarms that are connected wirelessly to the user's mobile phone or tablet, allowing him to monitor the condition of his home all the time, wherever the owner is. Of course, we do not need to analyze that a hacker can do just that by simply invading the network.
- Smartphones

Just think of all the spy gadgets the incredible Q has ever invented in the James Bond movies: microphones and sound recording systems, camouflaged microcameras, geolocation devices, programs that can steal personal data, bank accounts, e-mails, and even to check interconnected devices.
Well, your smartphone now has all these features! Which of course can be intercepted by hackers and make things look like science fiction. And as if that were not enough, the US military revealed two years ago that it has built an application (PlaceRaider) that uses the mobile phone camera and GPS data to create a three-dimensional model of the user's environment! Are you saying that the US military is the only one scamming such applications?
- Tablets and computers

If our smartphone can do that, what do you say our even more powerful computer can do? At a time when the cell phone may be spying on us, tablets, laptops and PCs are just as comfortable doing the same. And even worse than the smartphone, we inadvertently fill our computers with even more sensitive data, from passwords and e-banking information to geo-located photos (you know!) And other things we would not want to be exposed to. And they are all vulnerable…
- Pacemakers and insulin pumps
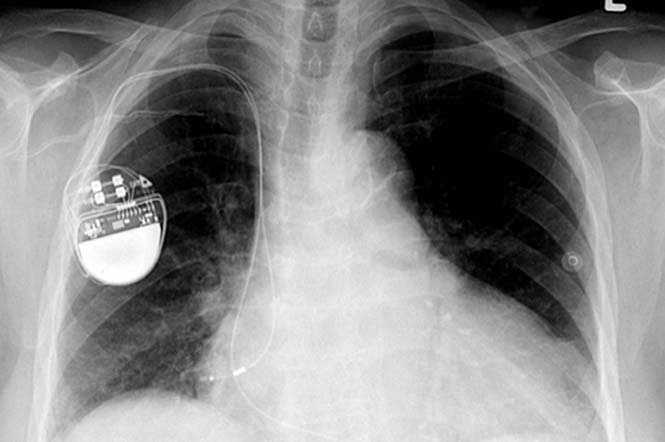
The icing on the cake! Who cares in the end for the hacking of their home when they can not feel safe even in their own body? It was in 2012 when hacker Barnaby Jack (White Hat) proved that he could kill a diabetic patient from 100 meters away by programming the insulin pump to deliver a lethal dose!
And the thing even further, now controlling pacemakers and implanted defibrillators. Let's hear what he has to say about his achievement: "These devices [pacemakers, insulin pumps, etc.] are computers that remain as vulnerable as your PC or Mac, even though they are not visible. When you actually check these devices, you are shocked by the vulnerability of their security "…
